| Table of contents | Previous page | Next page |
The log file view is selected via the tab "Log View". This tab does not offer further configuration options but allows easy access to all log files created for the current job. You'll see a table that holds all available log files and their respective execution dates and backup results for the currently loaded job. The table is sorted by the execution date of the job, most recent entries are at the top of the list.
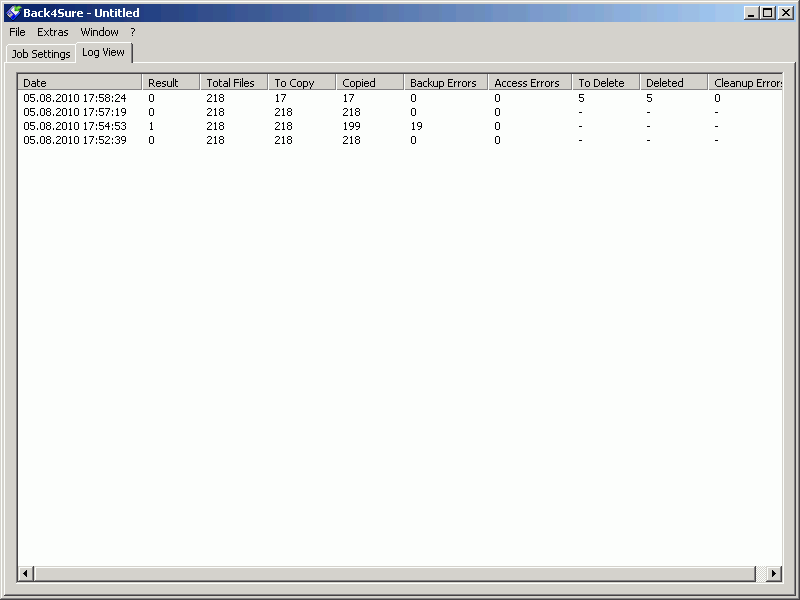
Figure 5.1: List of available log files for the current job
The columns of the table hold the following information:
| Column | Content |
|---|---|
| Date | Date and time of the job execution |
| Result | Numerical result code of the job execution, 0 means no error |
| Total Files | Number of files included in this backup job |
| To Copy | Number of files to be copied to the backup target |
| Copied | Number of files that were successfully copied during this execution |
| Backup Errors | Number of files that were not copied due to an error |
| Access Errors | Number of source folders that cannot be accessed due to missing access rights |
| To Delete | Number of orphaned files in the backup target |
| Deleted | Number of files that were successfully deleted during the cleanup run |
| Cleanup Errors | Number of files that were not deleted due to an error |
The entries will show you at a glance, if a backup job was successfully executed. In this case, the value 0 must appear under the column "Result". Any other value means that there was a more or less severe error during execution. You should take a look into the "Backup Errors" column, then, to see how many files weren't copied. If there are just one or two errors, the affected files were probably locked during execution. A larger number of copy errors indicate a more severe problem. If the counter for access errors is not zero, the overall backup result will also indicate the failure. In any case, you should take a look into the log file to see the cause for the malfunction.
If your system is configured to open log files with a text editor, you can open the log file by simply double clicking the entry in the table. If your system currently doesn't know how to handle log files, Back4Sure will automatically start the appropriate Windows configuration dialog if you double click on a log file in the list.
Attention! If you see only some hodgepodge when opening a log file, your text editor is probably not capable of displaying unicode files correctly. Use the Windows Notepad or some other unicode capable program like Notepad++ in this case.
Attention! If the format option is set to "Human readable" and you switch the program language from English to German, the column contents of the log file view will not be displayed correctly for older logs. Back4Sure cannot interpret the entries of the log file if they have a different language. Also do not rename the log files, as they wouldn't appear in the log file view anymore.
At each execution of a backup job a log file is created, which contains, depending on the log file settings, a summary or a complete list of all actions taken during the backup run. Chapter 3.8 describes in detail how to customize the content of the log file.
Log files may be created in a human readable format or in a format optimized for automated analysis. The information of both formats is identical, only the data representation varies. The following two chapters will help you to interpret the log file content.
The human readable log file has up to seven sections, each containing different aspects of the performed actions. A section always starts with a headline which is enclosed by three asterisks for easy recognition. Following sections exist:
| Section | Content | ||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| *** Job Summary *** | This is the summary of the job execution. Here you'll find the execution date and time, the backup duration and the overall result code. This should be the first section to look at. If the result code is 0, the backup was executed without any error. Possible result codes are:
|
||||||||||||||||||||
| *** Backup Summary *** | This is the summary of all backup activities. This section holds the following entries:
|
||||||||||||||||||||
| *** Cleanup Summary *** | This is the summary of all cleanup activities. This section will only be created if there actually was a cleanup run. This section holds the following entries:
|
||||||||||||||||||||
| *** Source Access Errors *** | Any directory selected for backup that cannot be accessed by Back4Sure will be denoted here. This section is only created if you have activated error logging in the logging options (chapter 3.8). Each entry consists of the full path of the inaccessible source folder and the result of the access operation as system code and plain text message. The result code is always non-zero, as only access errors are recorded here. There are usually only two possible error codes, either code 3 (The system cannot find the path specified) or code 5 (Access is denied). Code 3 results from source folders, that were selected for backup but deleted during the backup process. You may fix this error by choosing "Check Job Consistency" from the "Extras" menu. The job file will be checked for invalid source directories, then. The system code 5 will appear, if you don't have sufficient rights to access one of the selected folders or subfolders of the current backup set. Under Windows Vista or Windows 7 e.g. not even the administrator has the right to view or read the profile folders of other users. In this case, you should restrict the job to your own profile folder and create backup jobs for all other users separately. |
||||||||||||||||||||
| *** Backup Errors *** | This section holds one entry for each failed copy attempt. It is only created if you have activated error logging in the logging options (chapter 3.8). Each entry consists of the full path of the source file, the full path of the target file, the state of the target file and herewith the reason for copying this file and finally the copy result as system code and plain text message. In this section the result code is always non-zero as only failed copy actions are recorded here. To list all possible system codes would go beyond the scope of this manual, but the most common reason for a failed copy attempt is probably the system code 32 (The process cannot access the file because it is being used by another process). This means, another program claims exclusive access rights to the file in question and prevents other programs from reading it. In this case, close all open programs and retry the backup operation. A different solution is to exclude certain file types (e.g. *.lock) from the backup job by defining an exclude filter (chapter 3.3). This way, the possibly locked files will not be included in the backup set. |
||||||||||||||||||||
| *** Cleanup Errors *** | If during a cleanup run certain files cannot be deleted from the target directory, they'll be noted here. This section will only exist if error logging is activated. Each entry consists of the automatically generated path of a source file that corresponds with an existing target file, the full path of the target file, the state of the source file (e.g. source file does not exist) and herewith the reason for deleting the target file and finally the deletion result as system code and plain text message. In this section the result code is always non-zero again as only failed actions are recorded here. A common reason for a deletion failure is represented by the system code 5 (Access denied). This error often results from a write protected target file which cannot be deleted. You can alter the cleanup options (chapter 3.5) to enforce the deletion of write protected files. |
||||||||||||||||||||
| *** Backup Actions *** | If you have enabled logging of all actions in the logging options, each successful copy operation will be denoted here. Each entry follows the same scheme as described in section *** Backup Errors ***" and holds the source file, the target file, the reason for copying and the copy result, which is always 0 (The Operation Completed Successfully) here. | ||||||||||||||||||||
| *** Cleanup Actions *** | This section will also only be created if you have enabled action logging in the logging options. For each successful file deletion an entry will be created, following the same scheme as described in section *** Cleanup Errors ***. Each entry consists of the automatically generated path of a source file that corresponds with an existing target file, the target file, the source state and the deletion result code, which is always 0 (The Operation Completed Successfully) here. |
Machine readable log files hold the same information as the human readable variant but all entries are created using the ini format and are also invariant against the chosen program language. This allows an easy and reliable way to read and analyze the log file using an external program. Following sections exist:
| Section | Content | ||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| [JobSummary] | Contain the summary of the backup job execution. Following keys are available:
|
||||||||||||||||||||||||||||||
| [BackupSummary] | This is the summary of all backup activities. Following keys are available:
|
||||||||||||||||||||||||||||||
| [CleanupSummary] | This is the summary of all cleanup activities. This section will only be created if there actually was a cleanup run. Following keys are available:
|
||||||||||||||||||||||||||||||
| [SourceAccessErrors] | Any directory selected for backup that cannot be accessed by Back4Sure will be denoted here. This section is only created if you have activated error logging in the logging options. All keys belonging to one entry will receive a consecutive number, starting from zero. In the following key description, the position of this number is marked with a "X". Each entry has the following keys:
|
||||||||||||||||||||||||||||||
| [BackupErrors] [BackupActions] |
In these two sections each copy operation will represented by one entry consisting of four keys. Failed operations will appear in section [BackupErrors], successful operations in section [BackupActions]. For these sections to be included in the log file, error and / or action logging must be activated in the logging options. All keys belonging to one entry will receive a consecutive number, starting from zero. In the following key description, the position of this number is marked with a "X". Each entry has the following keys:
|
||||||||||||||||||||||||||||||
| [CleanupErrors] [CleanupActions] |
During a cleanup run, each file deletion will create one entry consisting of four keys. Failed operations will appear in section [CleanupErrors], successful operations in section [CleanupActions]. For these sections to be included in the log file, error and / or action logging must be activated in the logging options. All keys belonging to one entry will receive a consecutive number, starting from zero. In the following key description, the position of this number is marked with a "X". Each entry has the following keys:
|
If compression is enabled for the current backup, the system codes for backup and copy operations may not always correspond to the return value of the GetLastError() function but can be replaced by return values of the compressor. Which codes are used depends on the respective error. Codes from the packer can be recognized by a set bit 29 of the result code (the code is greater than 536870912). The currently used compressor has the following return values:
| Code | Meaning |
|---|---|
| 0 | The operation completed successfully. |
| 536870913 | Warnings were issued. |
| 536870914 | Fatal error. |
| 536870919 | Command line error. |
| 536870920 | Out of memory. |
| 536870921 | Can't create list file for archive operation. |
| 536871167 | Operation aborted by user. |
| Table of contents | Previous page | Next page |